XMPP over TOR with Jitsi
To increase security of your XMPP communication, potentially improve anonymity or avoid traffic filtering, it is possible to configure your XMPP client to work with TOR.
In this article I am describing how to configure Jitsi communicator to work over a connection provided by a TOR service on Linux. As usually I will take Ubuntu Linux as an example, but instructions often apply to other platforms as well.
Installing the software
First, let's install the required software.

We will install a nightly build version of Jitsi, which, as practice shows, is stable enough and has most recent features and bug fixes.
Disclaimer On this web site you might read about
or get access to various kinds of software and technology, including but not limited to libraries,
operating systems, software for communications, mobile phones and tablets,
Android software and Linux, even cars and motorcycles, security and penetration testing software,
software used in security research and forensics, some samples of software which can be
used (elsewhere) for malicious or illegal purposes. You will read about or be provided with
the ways to change it, to operate it and to use it. You might find advice and recommendations,
which are only an opinion, and not a legal advice or commercial recommendation..
Bear in mind, please, that everything you do, you do solely at your own risk
and responsibility. In no way the author of this web site, information, graphics
and other materials presented here or related to it can be made liable or
anyhow else responsible for your own actions as well as
actions of any third party and their direct or indirect results or consequences
with or without the use of this information as well as the software,
technology and systems mentioned and/or presented here,
no matter if developed by the author or by any third party.
In no way it is guaranteed that you will meet any suitability for
any particular purpose, safety, security, legality or even simply
functioning of the software and systems described here. You have to make
sure each time yourself, whether what you do, is really what you intend to
do, and that you are ready to be yourself responsible for. All the recommendations
and experiences described here are the opinions of corresponding authors and
are to be taken with care and own full responsibility.
The software provided
on or through this web site, linked to from this web site or anyhow else
related to this web site is provided by the corresponding authors on their
own terms. We provide all the software here as is without any guarantees to you.
You are responsible for deciding whether it is suitable for you or not.
You are also responsible for all direct or indirect consequences of using this
software.
Other web sites linked to from the current one are out of the author's control,
we can not guarantee anything about their content, its quality or even legality. We
can not be liable for any use of the linked to web sites or of the information presented there.
We reasonably try to keep this website running smoothly and to deliver
information to the best of our knowledge corresponding to the state of the art at the times
when the information is composed, usually presented together with the information, and out of good intents.
We can not however guarantee and can not be liable for this website being temporarily or permanently
unavailable, presenting unreliable information or software, or any other similar or not malfunctioning
or functioning not up to your expectations as well as any consequences
which might result from this site's operation.
sudo bash -c "echo 'deb http://download.jitsi.org/nightly/deb unstable/' >> /etc/apt/sources.list"
sudo apt-get update
sudo apt-get install jitsi tor
Update: we found out, that proxying is not working when using Jitsi with OpenJDK 7. If you use it, you'll have to update to OpenJDK 8 first. Install it, and the select as the default java to use.
sudo apt-get install openjdk-8-jre
sudo update-alternatives --config java
Next some configuration has to take place.
After you start Jitsi, you have to set up your XMPP account. Next, in the Options you can find Advanced tab, where a Global Proxy may be specified. Jitsi has proven to work fine with TOR over SOCKS4 protocol. SOCKS5 does not work for some reason. Set it up with the Proxy Server localhost and Proxy port 9050 as the image below shows.
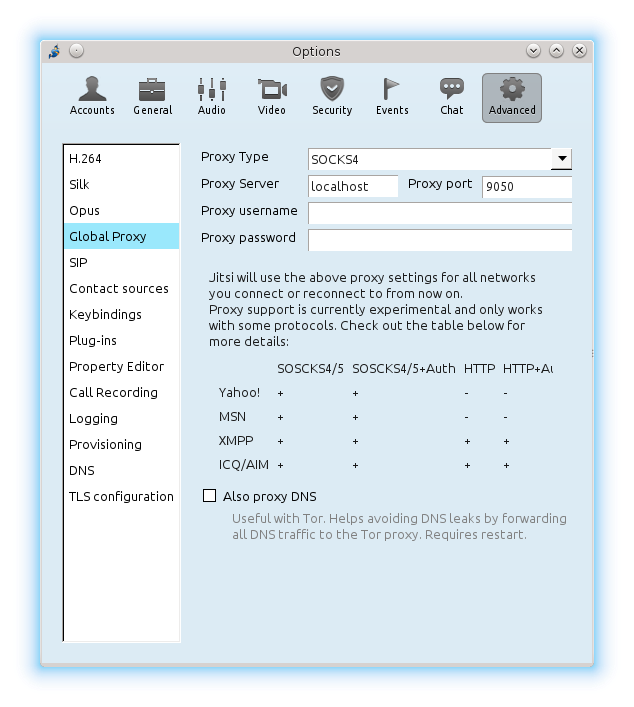
Afterwards Jitsi has to reconnect and continue working just how it was but over TOR. Congrats!
Discussing Solution
There are a number of points important to understand about the solution to tunnel XMPP over TOR. They cover a number of questions about Jitsi, TOR and their use in the combination.
First of all it is important to understand how TOR works and what kind of anonymity it gives to you. Namely, the information you send out is encrypted and passed over several hops. The last node decrypts your information and forwards it to the target machine. Like this you are "anonymized" for the target machine, in this case for the XMPP server you use. Next, XMPP server responds to the last node, and hops are made back to you. An important concern here obviously is that you have to login to the XMPP server. Thus you are de-anonymized to the degree your login credentials uncover your identity.
Second, TOR is known to be insecure due to the ultimate issues of the IP protocol which is not designed to provide anonymity. TOR attempts to build an additional layer on top of IP to provide anonymity. Still, due to the nature of the underlying protocol TOR can be deanonymized! Breaking TOR anonymity is especially practical when a state-like or provider-like big player is after you.
Third, Jitsi (and other communicators) do not only produce XMPP traffic, other traffic kinds might benefit more from anonymization. For example Jitsi can load an image when a link to it is dropped in the chat. A video thumbnail from YouTube can be loaded as well, if you turn it on in the options. When you are using TOR as a proxy, the loading of these side resources will happen with a higher degree of anonymity. Additionally you could click the check-box (see the figure above) and forward DNS lookups through the proxy, as the configuration dialog hints you in gray.
Finally, while texting is not a traffic-heavy operation, VoIP connections might suffer on performance when tunneled through TOR. So if you use VoIP often TOR-proxying might not be the best way to go.
Images copyright information
The first image on this website page was taken from: https://commons.wikimedia.org/wiki/File:Logo_Jitsi.svgIt is licensed under Creative Commons Attribution-Share Alike 3.0 Unported license: https://creativecommons.org/licenses/by-sa/3.0/deed.en
The second image is originally produced and you are free to make use of it under Creative Commons Attribution 4.0 International License: http://creativecommons.org/licenses/by/4.0/
Thanks for reading my blog!
 molotnikov.de
molotnikov.de