Let's Encrypt Launched!
Let's Encrypt was launched in beta mode a couple of days ago! Isn't it great? This might be a turning point in the history of HTTPS. From now on it indeed costs nothing. Congratulations to you all!
In the meanwhile I managed to try let's encrypt tool on my websites and figured out a bunch of tricks you might want to know too when switching to HTTPS for free with Let's Encrypt.
Basically the installation of Let's Encrypt certificate is very straightforward.
It is described
here.

What the automated installer does is going into /etc/apache2/sites-available and creating an HTTPS copy of every site detected. There are some underwater stones on its way. Here I describe how to make things easier for the (great!) installer and finish up your migration to HTTPS gracefully.
Disclaimer On this web site you might read about
or get access to various kinds of software and technology, including but not limited to libraries,
operating systems, software for communications, mobile phones and tablets,
Android software and Linux, even cars and motorcycles, security and penetration testing software,
software used in security research and forensics, some samples of software which can be
used (elsewhere) for malicious or illegal purposes. You will read about or be provided with
the ways to change it, to operate it and to use it. You might find advice and recommendations,
which are only an opinion, and not a legal advice or commercial recommendation..
Bear in mind, please, that everything you do, you do solely at your own risk
and responsibility. In no way the author of this web site, information, graphics
and other materials presented here or related to it can be made liable or
anyhow else responsible for your own actions as well as
actions of any third party and their direct or indirect results or consequences
with or without the use of this information as well as the software,
technology and systems mentioned and/or presented here,
no matter if developed by the author or by any third party.
In no way it is guaranteed that you will meet any suitability for
any particular purpose, safety, security, legality or even simply
functioning of the software and systems described here. You have to make
sure each time yourself, whether what you do, is really what you intend to
do, and that you are ready to be yourself responsible for. All the recommendations
and experiences described here are the opinions of corresponding authors and
are to be taken with care and own full responsibility.
The software provided
on or through this web site, linked to from this web site or anyhow else
related to this web site is provided by the corresponding authors on their
own terms. We provide all the software here as is without any guarantees to you.
You are responsible for deciding whether it is suitable for you or not.
You are also responsible for all direct or indirect consequences of using this
software.
Other web sites linked to from the current one are out of the author's control,
we can not guarantee anything about their content, its quality or even legality. We
can not be liable for any use of the linked to web sites or of the information presented there.
We reasonably try to keep this website running smoothly and to deliver
information to the best of our knowledge corresponding to the state of the art at the times
when the information is composed, usually presented together with the information, and out of good intents.
We can not however guarantee and can not be liable for this website being temporarily or permanently
unavailable, presenting unreliable information or software, or any other similar or not malfunctioning
or functioning not up to your expectations as well as any consequences
which might result from this site's operation.
Existing Self-Signed Certificates
Many of you have already self-signed certificates on your (hobby-) sites and thus SSL versions of the configurations.
My advise would be to move the SSL-enabled site configurations away for a while when installing let's encrypt client. Once let's encrypt has done the job new SSL-enabled site configurations will be created. Modify them to correspond to your existing SSL-configured sites which you moved away after the installer has done the job.
Redirects to HTTPS
If you had already redirects from HTTP to HTTPS configured, make sure that the let's encrypt installer has not simply copied these redirects into the secured site configurations.
If so, your site will stop loading because of infinite redirect loop.
Tricks with HSTS
You could read more about HTTP Strict Transport Security (HSTS) here on Wikipedia, but what it essentially does is that it tells your browser to remember that your website works with HTTPS. This is done to prevent security downgrade attacks (or mistakes) which could lead to connecting to the website over HTTP once it is known that HTTPS is supported.
The trick is, that some browsers might accept HSTS rules for your main domain, like molotnikov.de in my case, and then refuse to work over HTTP with its subdomains, like dance.molotnikov.de.
To avoid this problem, make sure you migrate all of your subdomains at once to HTTPS.
The www Subdomain
When generating certificates, make sure to generate certs for the www.yoursite.com subdomain, since it is often used by the web server. If you have www subdomain active this is something you have to do. A simple test of the SSL settings for your website will reveal this detail among others: link to ssllabs.com.
To handle both your domains you could use this command:
cd letsencrypt
./letsencrypt-auto -d mydomain.com -d www.mydomain.com
Replace mydomain.com with your domain name.
Usually these commands are run with root privileges. This is not a must in principle to make use of let's encrypt. There is another let's encrypt client which works without sudo-ing.
Insecure Links to Resources
Together with reconfiguring Apache, you want to change the content as well to embed only secure links to the resources. Otherwise you (or, worse, your visitors) will face mixed content blocking warnings when visiting your website. Read more about it on the Mozilla website here.
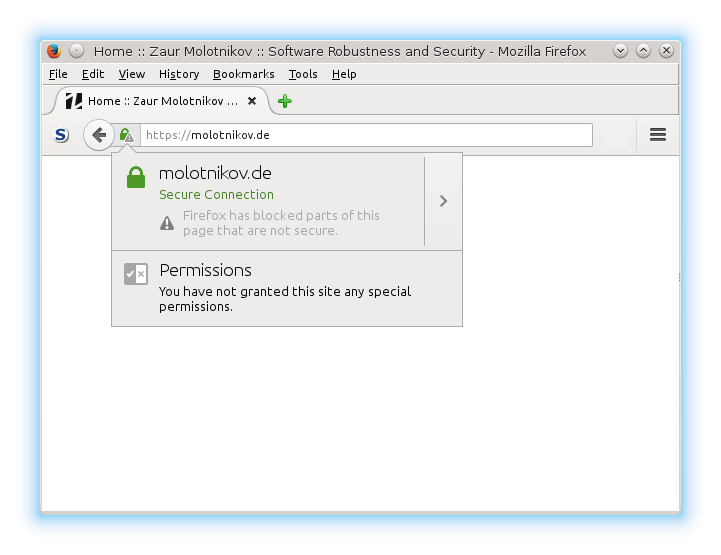
Essentially your clever browser will avoid insecure HTTP connections from the secure address you have in the address bar. These connections might include links to images, style sheets, scripts and other resources your site has to load. Update them to HTTPS to avoid mixed content blocking and related warnings.
A tricky part in this process might be http://... links in CSS. Make sure you update them to HTTPS too.
Web Console of Firefox is your friend in this scrutiny: it will show you which insecure connections were blocked
Afterword
Now let's wish Let's Encrypt a lot of success in the future, and hope that the unbelievable ease of use of let's encrypt automated client does not anyhow bring insecurities to our web servers and their visitors! :)
The future will show us, but right now HTTPS is definitely an upgrade to an HTTP-only website's security. So go ahead, it shouldn't take more than an hour of your time for a small website as long as you keep focused!
Images copyright information
The first image on this website page was taken from: https://letsencrypt.org/It is licensed under Creative Commons Attribution 3.0 International license: http://creativecommons.org/licenses/by/3.0/
The second image is originally produced and you are free to make use of it under Creative Commons Attribution 4.0 International License: http://creativecommons.org/licenses/by/4.0/
Thanks for reading my blog!
 molotnikov.de
molotnikov.de