Using Tor Bridges with Tor Daemon
Finally my Tor connections got filtered out by one ISP. I use Tor as a standalone daemon on my Ubuntu machine. Unfortunately, I couldn't find one single page describing all the configuration you need to start using bridges with Tor service on Debian. So I have created one.
In this article you'll find all the information you need to configure bridges on your Tor service on Debian to use them as a client. E.g. we will not create a bridge, we will just use some existing bridges to get around the blocks our ISP (tried to) undemocratically enforced on us.

What are Tor Bridges
Shortly, bridges are Tor nodes not listed in the public directory. It means an ISP blocking Tor will highly likely not block the bridge nodes. Until they are not blocked we can continue using Tor connecting to one of the bridges. Once ISP detects bridges and blocks them, we ask for new bridges and continue. The arm race repeats.
If you are using Tor Browser Bundle it is extremely easy to configure it to use bridges. Just follow the manual on this page: https://www.torproject.org/docs/bridges.html.en. Below I describe how to configure your Tor running in a daemon mode on a Debian machine.
Getting Bridge Lines
So now when you know what Tor bridges are for, we want to go and grab a few addresses of them. For this go to this page: https://bridges.torproject.org/bridges.
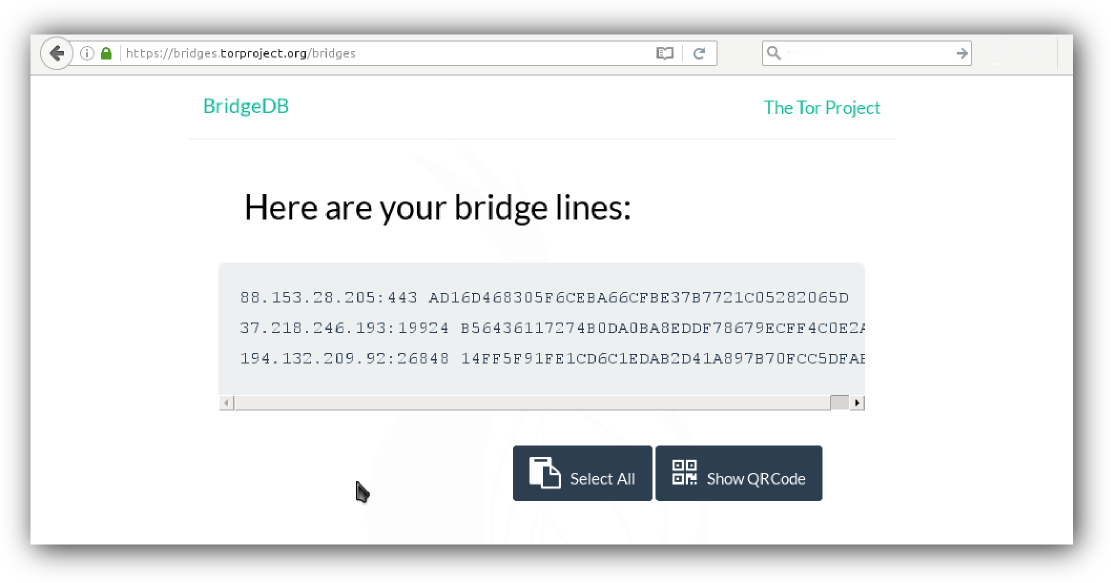
After entering a captcha text you should get three legacy IPv4 addresses of three bridge nodes and their fingerprints. This information will be needed further in the configuration stage, so we copy it to clipboard.
Setting up software
Now we set up Tor service and obsf4 transport to use bridges.
Disclaimer On this web site you might read about
or get access to various kinds of software and technology, including but not limited to libraries,
operating systems, software for communications, mobile phones and tablets,
Android software and Linux, even cars and motorcycles, security and penetration testing software,
software used in security research and forensics, some samples of software which can be
used (elsewhere) for malicious or illegal purposes. You will read about or be provided with
the ways to change it, to operate it and to use it. You might find advice and recommendations,
which are only an opinion, and not a legal advice or commercial recommendation..
Bear in mind, please, that everything you do, you do solely at your own risk
and responsibility. In no way the author of this web site, information, graphics
and other materials presented here or related to it can be made liable or
anyhow else responsible for your own actions as well as
actions of any third party and their direct or indirect results or consequences
with or without the use of this information as well as the software,
technology and systems mentioned and/or presented here,
no matter if developed by the author or by any third party.
In no way it is guaranteed that you will meet any suitability for
any particular purpose, safety, security, legality or even simply
functioning of the software and systems described here. You have to make
sure each time yourself, whether what you do, is really what you intend to
do, and that you are ready to be yourself responsible for. All the recommendations
and experiences described here are the opinions of corresponding authors and
are to be taken with care and own full responsibility.
The software provided
on or through this web site, linked to from this web site or anyhow else
related to this web site is provided by the corresponding authors on their
own terms. We provide all the software here as is without any guarantees to you.
You are responsible for deciding whether it is suitable for you or not.
You are also responsible for all direct or indirect consequences of using this
software.
Other web sites linked to from the current one are out of the author's control,
we can not guarantee anything about their content, its quality or even legality. We
can not be liable for any use of the linked to web sites or of the information presented there.
We reasonably try to keep this website running smoothly and to deliver
information to the best of our knowledge corresponding to the state of the art at the times
when the information is composed, usually presented together with the information, and out of good intents.
We can not however guarantee and can not be liable for this website being temporarily or permanently
unavailable, presenting unreliable information or software, or any other similar or not malfunctioning
or functioning not up to your expectations as well as any consequences
which might result from this site's operation.
Most likely, if you read this article, you have a Tor service installed already. Otherwise:
sudo apt-get install tor
Next we install OBSF4 transport. It is needed to connect to bridges./p> Edit your /etc/apt/sources.list to contain these lines:
# Tor Bridges deb http://deb.torproject.org/torproject.org obfs4proxy main
Update package lists, and install the software:
sudo apt-get update
sudo apt-get install obfs4proxy
Now we are ready to configure the Tor daemon.
Tor configuration
We now go to the /etc/tor/torrc file and add the following lines:
UseBridges 1
# Your bridges from above step here, do not copy this information directly!
Bridge 88.153.28.205:443 AD16D468305F6CEBA66CFBE37B7721C05282065D
Bridge 37.218.246.193:19924 B56436117274B0DA0BA8EDDF78679ECFF4C0E2AA
Bridge 194.132.209.92:26848 14FF5F91FE1CD6C1EDAB2D41A897B70FCC5DFAFA
ServerTransportPlugin obfs4 exec /usr/bin/obfs4proxy
In the configuration you will have to insert the copied bridge lines from the step above and prepend them with the word "Bridge" on each line as shown above.
You might also try using the bridges which I got and pasted here, but they are likely to be blocked by the time you read this article.
Restart the Tor service and check the log file for problems.
sudo service tor restart&
sudo tail -f /var/log/tor/log
...
You should be able to continue using Tor now despite the ISP blocks.
Once the bridges you use get blocked, you can request and configure new ones, exactly as it is described in this article once again.
Security
Now, there is a lot written about Tor's security and security of bridges. What is important to tell maybe is that Tor bridges are nothing more than not highly advertised Tor nodes. It is possible to discover them still and an arm race is also going on in discovering them and fighting the discovery.
Tor can be conveniently used as a daemon in a situation when you need to route other than browser programs. For example XMPP, as I describe here.
For a number of reasons, it is still more secure to use Tor browser, then your regular browser routed through Tor when browsing online. Hardened settings and right plug-ins installed in the customized Firefox make the browsing safer.
Images copyright information
The first image on this website page was taken from: https://en.wikipedia.org/wiki/Arch_bridge#/media/File:Gaoliang_Bridge.JPGIt is licensed under Creative Commons Attribution-ShareAlike 3.0 Unported (CC BY-SA 3.0) license: https://creativecommons.org/licenses/by-sa/3.0/
The second image on this page is a screenshot I made.
You are free to reuse it under Creative Commons Attribution 4.0 International (CC BY 4.0) license: https://creativecommons.org/licenses/by/4.0/
Thanks for reading my blog!
 molotnikov.de
molotnikov.de